From Dev Pulse 62:
Blockquote Our approach to these concerns is to design everything in Holo with the ultimate goal of decentralizing every component, mitigating the risks involved with giving anyone gatekeeper powers. Principally, this relates to how HoloPorts connect to one another. HoloPorts are connected via a peer-to-peer VPN to form an internal network, which is why Holo Hosts do not need static IPs.
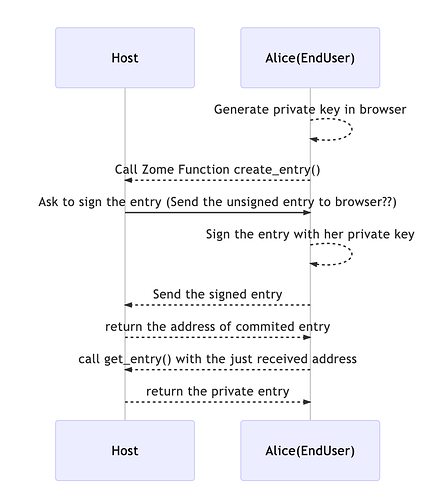
Holo’s gateways then route a web user’s traffic to their assigned hosts. In many traditional client-server architectures, encryption would be ‘terminated’ at the gateway—it would hold the SSL certificate allowing it to decrypt user data and forward it to the server. On the Holo network, encryption only terminates when data arrives or leaves the HoloPort. Each HoloPort provisions its own personal certificate without involving the Holo gateways. The gateways themselves use Server Name Indication (SNI) extensions to route data without needing to decrypt it, making it impossible for the gateways to snoop on users, since everything passing through is end-to-end encrypted. Each web user is assigned to multiple redundant HoloPorts, distributed across the globe rather than concentrated in a few data centers owned by one company. In fact, two copies of one user’s data aren’t even guaranteed to be in the same country. Each HoloPort is only responsible for a subset of users, making the network more resilient and reducing the power of any one hosting provider. Furthermore, Holo’s gateway servers run on globally distributed hosting infrastructure, which makes them resilient to high traffic spikes or denial-of-service (DoS) attacks."
So, one question (for me) becomes: What is a “gateway,” and how do HoloPorts relate to them; and then also, like everyone else is asking, to what degree can Holoport operators “read” (view) users’ data.
Which brings up some very interesting, and crucial/ salient questions and issues not only within Holo, but distributed computing and the “new internet” being built in general…
First of all, let’s compare with some of the systems we are familiar with: Ethereum and Bitcoin. In both of these, “hosts” (i.e., Miners, and, depending on your philosophical bent, Full nodes as well) hosts can absolutely “see” all of the data running through their system - that’s part of the entire point!! This is the irony, in my opinion, of the supposed “fud” to begin with… little do most consider, but, pretty much the same exact thing they are ostensibly fudding Holo Holo for, occurs in Bitcoin and Ethereum!!
A “decentralized internet” might look very different than the one we have now… The intriguing thing which comes up, though, is: Do people even really want the “freedom” and autonomy they speak of - or, is it more just the idea they’re in love with… For example, prima facie, many might answer that “Oh, I don’t want “big brother” sniffing around my data, ‘Controlling it…’” But when faced with the alternatives, such as: yourself, or even your neighbor- these bring with them a whole new slew of problems!! Funny thing being, when you think on it, maybe I would rather have Jeff Bezos “control” my data instead of my next door neighbor!! Or even myself ! (As I’m lazy, not knowledgeable, etc etc.)…
So as sort of bizarre and "scary " of a concept that “gasp! OTHERS will be seeing my data!!!” Low and behold, they never cared before!!! But as the content of said data shifts from a bunch of random numbers to actual “intelligible” tweets, texts, and beyond… Now it’s starting to become a bit more serious.
That being said, continuing with the BTC comparison: although not totally anonymous, BTC is "pseudo-anonymous: i.e., I might see the data, but I don’t know to whom it belongs… This is how I envision Holo to also operate. (But I am not a dev and do not know much about this.) I.e., yes, if a host had such a desire to root around in her machine, maybe they could “see” data… but to them it would probably look like a jumbled mess. (but I don’t know).
And while on the subject, perhaps someone could implement many of the “Zero-knowledge” proof schemas coming out. It’s a fascinating technology, imo, and we’re only seeing the beginning. But if that could be worked into Holo… we’d have a truly “unenclosable carrier!!”
ALSO (lotta alsos): And I know this will likely get a lot of “guff” from the more conservative in the community, but, yes, at a certain point, it is quite likely, in this day and age at least, that you WILL have to “defer to law,” etc. in order to solve some issues: in this instance, quite possibly the very topic we’re discussing: if someone were to tamper with or alter/ mess up/ damage or otherwise harm another’s data, they would be held just as accountable as, say, Amazon, facebook, or the like. In fact, within the Holo(chain) ecosystem, I would venture to say, because of its very structure (decentralized, granular) not only would it likely be even easier to discover malicious acts or actors, but this fact itself would likely act as a deterrent to shenanigans. (In other words, because everything is much more agent -centric, everyone is much more accountable - I think I’m preaching to the choir on much of this, though).


 ) Here’s all I can think of:
) Here’s all I can think of: